Remote work has seen a sharp rise across Southern Ohio, from suburban homes near Cincinnati to the quieter stretches of Jackson and Gallia counties. While the flexibility, reduced commuting, and lower overhead costs are hard to ignore, an unsettling truth lingers behind the shift: many people are now working from home with internet setups that were never designed for professional use.
Home networks, often set up for streaming and shopping, simply weren’t built to support the security demands of modern telework.
Why Proxy Checkers Deserve A Spot In Your Security Stack
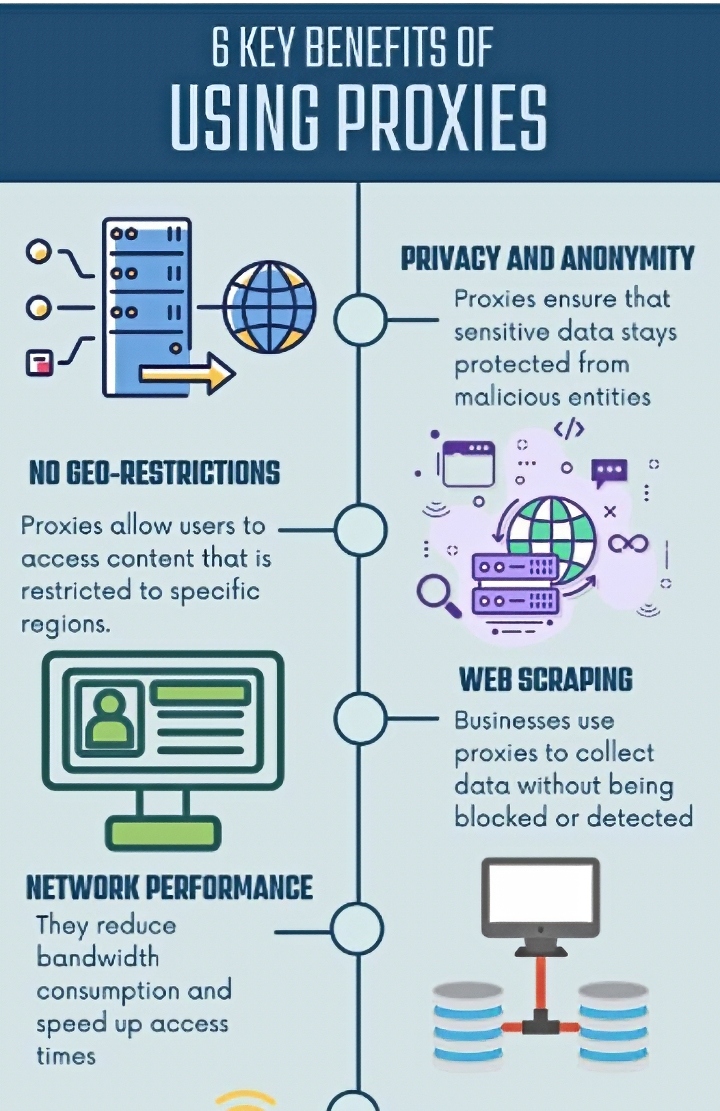
A proxy checker may sound like tools for coders or cybersecurity analysts, but they’ve quietly become essential for anyone working from home.
A proxy server acts as a middleman between your computer and the websites or services you use. It helps mask your IP address, enabling privacy, geo-targeted access, and added layers of anonymity. Proxies—especially free or public ones—can be misconfigured, slow, or even malicious. That’s where proxy checkers come in.
These tools inspect whether the proxies you use are functional, secure, and truly anonymous. For example, a remote insurance adjuster using third-party web tools with a proxy may unknowingly reveal their real IP, location, or login credentials—if the proxy isn’t secure. Proxy checkers flag these vulnerabilities in real time.
The Hidden Vulnerabilities Of Rural And Suburban Internet Setups
Most Southern Ohio homes weren’t designed with cybersecurity in mind. And when remote work is layered onto a network meant for casual streaming and shopping, cracks begin to show.
Many broadband connections in towns like Waverly, West Union, or McArthur still rely on older routers and default ISP configurations. These routers may have outdated firmware, weak administrative passwords, or unsecured guest networks. Add in the common habit of letting multiple household devices share one network—and you’ve got a cocktail of vulnerabilities.
ISPs in the region often offer minimal built-in security beyond a generic firewall. That means it’s up to the user to manually install network encryption, segment guest devices from work hardware, and monitor for strange traffic behavior. Few do.
The consequence? Malware can spread quickly across devices. A phishing email opened on a teenager’s laptop could allow a hacker lateral movement to access your work files. Worse still, ransomware targeting VPN tunnels has been increasingly aimed at remote workers in lightly protected environments.
Investing in upgraded routers, enabling WPA3 encryption, and disabling remote access features you don’t need can greatly improve your home setup’s resilience.
Weak Password Habits: A Cybercriminal’s Dream
It’s not just your network hardware that needs attention—it’s your login credentials, too.
Data from 2024 suggests that over 61% of home workers in the U.S. still reuse the same passwords across multiple platforms. In Southern Ohio, where many professionals juggle local business accounts, healthcare portals, and school systems, password fatigue leads to shortcuts.
The danger is compounded by the increased use of shared cloud services. A weak password on a file-sharing app or CRM system could allow a data breach that impacts hundreds of clients—not just one household.
One of the easiest defenses is enabling multi-factor authentication (MFA). While many users still avoid it for convenience, MFA reduces the risk of unauthorized logins by up to 99.9%, according to Microsoft.
Password managers like Bitwarden or 1Password, paired with MFA, ensure that even if a breach occurs, your credentials aren’t easy to replicate. And for Southern Ohio workers handling sensitive data (e.g., tax prep, medical forms, legal documents), that layer of protection is increasingly becoming a necessity, not a luxury.
The Rise Of Remote Phishing In Local Networks
Phishing scams have evolved, and now they’re specifically targeting remote workers in suburban and rural areas.
Southern Ohio saw a 16% rise in phishing-related complaints filed with the FCC in 2023. Why? Because local targets often lack company-wide security training and may not recognize sophisticated social engineering attempts. One well-crafted email appearing to come from a bank, a delivery service, or a client can convince a user to click—and expose their machine to spyware or credential harvesting scripts.
What makes phishing even more effective now is the blend of personal and work usage on the same devices. A remote worker might check a work email, then switch tabs to a personal Gmail account or shopping site. A phishing link clicked while browsing a personal account could still infect the device used for work.
To stay safe, remote workers should:
- Use browser extensions that warn against known phishing domains (like Netcraft or uBlock Origin)
- Run regular scans with antimalware tools like Malwarebytes
- Separate personal and professional browser profiles
More importantly, anyone working remotely should routinely attend cybersecurity training—even if self-led—every six months.
Insecure Video Conferencing: A Leak Waiting To Happen
Video conferencing has become a lifeline for collaboration, but it’s also a weak spot for many work-from-home users in Southern Ohio.
Many default video call apps do not enable end-to-end encryption. If you’re discussing legal strategy, financial plans, or medical consultations on platforms like Zoom, Google Meet, or Skype, you need to know exactly how protected that call is.
Zoom, for instance, only offers true end-to-end encryption in its advanced settings or paid tiers. But many users in smaller towns—from Lucasville to Jackson—use the free version. Without adjusting security settings or using a secure meeting ID protocol, your conversation could be intercepted, or worse, accessed via meeting bombing.
Protect yourself by:
- Always using waiting rooms or authentication-enabled logins
- Avoiding screen sharing unless absolutely necessary
- Never discussing sensitive personal or client data on an unsecured line
Organizations can also invest in platforms like Signal or Microsoft Teams Premium, which prioritize security over ease of access.

Endnote
Southern Ohio’s work-from-home boom isn’t slowing down—but neither are the threats that come with it. Proxy checkers provide a first line of defense for anyone using anonymized connections, but broader risks—ranging from phishing and poor password hygiene to insecure routers and smart-home vulnerabilities—must be addressed too.